Cloud File Sharing: Secure Ways to Send Large Video Files
Sending multi-GB video files? Learn secure methods for large-file delivery - presigned URLs, managed transfer (Aspera/Signiant), resumable uploads (tus), E2EE providers, watermarking, and a fail-safe checklist for creative teams.
Why security matters (and why large video files are a different problem)
Big video files are routine for creative teams, but they carry special risks: long uploads that can fail, accidental public exposure of unreleased footage, and costly re-uploads if integrity is lost mid-transfer. Security for large-file workflows isn’t just encryption - it’s access control, auditability, robust transport, and leak deterrents like watermarking. Below are practical, field-tested ways to send large video files while keeping them secure and avoiding wasted time.
The secure options - short primer (what each method actually does)
Presigned URLs (cloud storage links) - temporary, signed links to a cloud object (S3-style). Fast and convenient for browser uploads/downloads, but security depends on short expiry, minimal permissions, and careful handling. AWS recommends strict guardrails when using presigned URLs (use short TTLs, restrict allowed operations, log usage). (Amazon Web Services)
Managed high-speed transfers (Aspera / Signiant / MASV) - use specialized transfer protocols optimized for throughput and reliability. These systems add encryption in transit, integrity checks, resumable transfers and enterprise reporting for compliance. Aspera’s guides document in-flight and at-rest encryption options for secure transfers. (ibmaspera)
Resumable HTTP uploads (tus protocol / Uppy / client libs) - for browser-based uploads that can resume after interruption. Services such as Cloudflare and Supabase support tus to avoid restarting multi-hour uploads from zero. This is a practical middle ground when you don’t need full Aspera-level throughput. (Cloudflare)
End-to-end encrypted (E2EE) sharing services (Tresorit, Proton Drive, Internxt) - providers that encrypt files client-side so the vendor can’t read the content. Great when confidentiality is paramount, but E2EE options can complicate server-side processing (e.g., proxy generation) unless the workflow is designed for it. (Proton)
Watermarking & forensic identifiers - embed visible or forensic (invisible, traceable) watermarks into review copies. Forensic watermarking lets studios trace leaks back to the source, which is a powerful deterrent for pre-release content. (Ci Blog)
Physical shipping (last-resort) - for multi-TB archives, shipping a hardened drive via secure courier still makes sense when bandwidth or cost makes online transfer impractical.
Security best practices - applied to large video files
Encrypt in transit and at rest. Use TLS for transfers and vendor/server-side AES-256 (or equivalent) at rest. Managed transfer providers and reputable cloud vendors provide encryption options by default. (See Aspera docs for in-flight and at-rest encryption options.)
Short-lived, permissioned presigned URLs only. If you use presigned links for uploads or downloads, issue them with minimal allowed actions and short expirations, and rotate credentials regularly. Monitor for unexpected downloads or repeated failures. AWS’s guidance on presigned URLs explains these guardrails.
Use resumable upload protocols for reliability. A multi-GB upload that restarts from zero wastes time and bandwidth; tus and client libraries (Uppy, tus-js-client) allow resuming partway through. Cloud docs such as Cloudflare and Supabase recommend tus for large assets.
Require strong access control and MFA. Use SSO, role-based access (project-scoped permissions), and multi-factor authentication for accounts that can access production masters. Log every access for later auditing.
Add watermarking to review copies. For client previews, use visible watermarks or forensic watermarking so leaks can be traced. This both deters leaks and gives legal/operational recourse when needed.
Verify integrity with checksums. Use checksums (MD5/SHA) to confirm uploads/downloads completed intact before deleting local copies. Managed-transfer systems and most cloud SDKs support integrity checks.
Restrict link lifetime and downloads. Set short TTLs for shared links, use password protection, and disable downloads where possible for sensitive previews.
Plan for a fallback. Keep local proxies or cached copies when a critical delivery is in progress (so reviewers can continue even if the cloud is slow or a region has problems).
When to pick what (practical decision map)
Scenario | Recommended approach |
|---|---|
One-off master delivery to a post house or broadcaster (TBs) | Managed transfer (Aspera/Signiant) or physical drive - integrity and speed matter. |
Frequent collaborator reviews with many small/medium files | Cloud sharing with presigned URLs + short TTL + resumable uploads for assets. Use audit logs and password-protected links. |
Highly sensitive or embargoed assets | E2EE provider or client-side encrypted workflow + watermarking for review copies. |
Browser-first uploads from contributors | Use tus/resumable uploads or a managed browser uploader (Uppy) to avoid restarts. |
Fast turnaround with remote reviewers and low bandwidth | Generate proxies server-side or locally, share streaming previews with watermarking. |
Quick vendor notes & tools (shortlist)
Aspera / Signiant / MASV - high-speed, enterprise-grade transfers with encryption and integrity checks; ideal for TB-scale deliveries.
S3 presigned URLs - convenient for uploads/downloads; make them short-lived and tightly permissioned.
tus / Uppy / client resumable libraries - essential for robust browser uploads. (Cloudflare, Supabase docs recommend tus for large assets.)
E2EE providers (Proton Drive, Tresorit) - for maximum confidentiality, but check whether their workflow supports proxies/watermarks for review.
Watermarking vendors (Moxion, Ci Media Cloud, internal tools) - forensic watermarks are standard for studio-level leak protection.
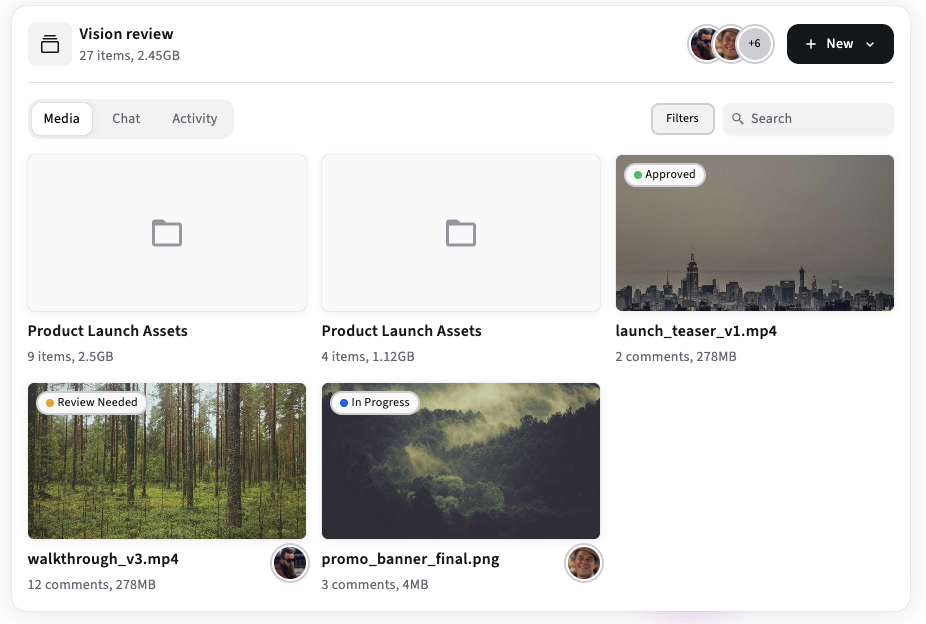
How a project-first workspace (like Kreatli) helps secure and streamline sharing
A good project workspace centralizes files, comments, versions, and access control - making it far easier to apply the controls above consistently:
Project-scoped permissions reduce accidental over-sharing (invite reviewers to the project/file, not the entire storage bucket).
Automated proxy + watermark generation (where available) means you never have to send full masters for review.
Built-in activity logs and approval gating make it simple to audit who saw what and when.
Quick fallback workflows (attach a local proxy or an exported package to the project) help teams keep reviewers working when transfers or cloud services lag.
If you want to test a secure sharing workflow end-to-end, run a pilot: configure short-lived presigned uploads for ingest, enable resumable uploads for contributors, auto-generate a watermarked proxy for reviewers, and test an Aspera transfer for master delivery - all coordinated inside a single project workspace so context, approvals and receipts are kept together.
Conclusion - summary & next step
Sending large video files securely is a systems problem, not just a tool choice. The right approach combines a fast, reliable transport (Aspera/Signiant or MASV for TBs), reliable resumable uploads for browser users (tus/Uppy), short-lived presigned links for controlled cloud access, watermarking for review copies, and strict access controls with audit logs. For most creative teams the practical sweet spot is a hybrid: use managed transfer for masters, cloud sharing + resumable uploads for collaboration, and a project-first workspace to centralize access, proxies, comments and audit trails.
If you want a safe place to pilot this: create a free Kreatli project, configure short-lived upload links for ingest, auto-generate watermarked proxies for reviewers, and run the 1-week pilot checklist above - you’ll see how much smoother and more secure your review cycles become.
Try a Secure Review Workflow
and start a free Kreatli project to generate a watermarked proxy in minutes.